In previous research, we have observed the poor record of online engagement of community councils in Scotland, though I doubt this is issue is restricted only to this context. With some notable exceptions, Community Council online presences are characterised by low activity. Only around a quarter are actively online whether on Facebook or web, and even when there are high levels of primary postings, there is low secondary engagement in the form of comments or responses, never mind sustained online debate.
This has been characterised as “lurking”.
The question I am exploring at the moment is:
To what extent is a passive audience (lurking) an issue to community representatives when they are posting material online?
One question this raises is why so few citizens participate online. This has been one theme of (e-participation) research into online democratic processes since the field began at the start of the millennium. There has been a build up of work considering non-participation (lurking) in an e-participation context (eg Edelmann & Cruickshank [1], but also Sevensson[8] etc). My last blog post gives an overview of approaches to lurkers.
Another question is why to some representatives persist in creating content online even in the face of low engagement.
What I want to discuss here is what are the available models for answering this question. (Caveat: bear in mind that since three-quarters of CC online presences are non-existent or not actively maintained – it is clear that the answer is that most don’t bother).
At the moment, this seems to break down into three separate sub-questions.
What expectations do these representatives have of their community?
There has been a body of work which uses research from work-based communities and organisational learning to understand, led by Wenger[10]. Does it make sense to use models and expectations of lurkers shaped by communities of practice (CoP) theory (eg in Takahashi’s work [9]) when understanding behaviours of lurkers relating to local communities? This matters, because research into communities of practice has an inherent “de-lurking” agenda – ie it’s always seen as good to bring more of the community out into (online) dialogue [6].
CoPs are units of organisational learning: as soon as this is written down, it’s obvious to see that this is a problematic assumption to make about local communities. It may make sense when looking at how community councillors learn to and sustain their use of online tools [2]. This doesn’t necessarily follow when talking about a real-world community of people with different interests and at different life-stages.
Why would someone post material online in the face of little response?
I can see two possible explanations. One comes from sense of duty arising out of perception of what is required of the role, and related to that, seeing the activity as part of reinforcing self-definition. This model of behaviour fits in with research into everyday information practices [7], and wider questions of how people express identity[4] and gives a framework for looking for how experience from everyday life or the workplace is being applied to the role of being a community councillor.
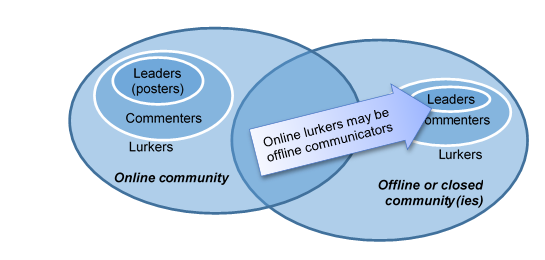
Another explanation of the acceptance of low responses might be that there is an expectation of responses through other channels, or that people will only respond to issues that affect them directly. This leads to further questions around channel choice and expectations of the different channels, online and offline, public and private [5] and the importance given to building up social capital [3] in local (offline) communities.
How does expectation of community shape the expectation of the role?
Perhaps the behaviours could be better understood by comparing activities to other local media. On the other hand, or maybe at the same time, models around the nature of ‘representation’ are more relevant: if a community councillor is representing their community, do they have to engage with all citizens? Maybe it’s enough to communicate information clearly through an (official) channel, and then engage with citizens who are concerned about a particular issue. As representatives, they would expect to make a judgement of how important/representatives the expressed concerns are: the representative is then imagining the lurkers, and ensuring their unexpressed viewpoints are taken into account.
To conclude: Local communities are not communities of practice, so it may be a category error to see lurkers as an issue in local communities online. Or at least, CoP-based models can only be partly helpful.
Acknowledgments
As before: Thanks to Noella Edelmann for her notes and insights into the knowledge management and organisational learning approaches to lurking (including as the implications of the Takehashi and Nonnecke & Preece papers). Thanks as ever to Bruce Ryan for helping with the data collection, and keeping the project moving. Some of this work was carried out in parallel with the IL-DEM project, which was funded by CILIP’s Information Literacy Group.
Footnote
This research is partly shaped by the simple fact that it’s easiest to research the content makers: this inherently excludes those who are not creating content, in particular, the citizens who are not engaging online. It is possible to reach community councillors – they can at least be contacted and invited to participate. We are currently in the process of gathering and analysing data from Community Councillors in Scotland.
References
[1] Cruickshank, P. et al. 2010. Signing an e-petition as a transition from lurking to participation. Electronic Government and Electronic Participation. J. Chappellet et al., eds. Linz, Austria: Trauner Verlag. 275–282.
[2] Cruickshank, P. and Ryan, B.M. 2015. The Communities of Practice model for understanding digital engagement by hyperlocal elected representatives. Electronic Government and Electronic Participation (2015), 11–18.
[3] Cullen, R. and Sommer, L. 2011. Participatory democracy and the value of online community networks: An exploration of online and offline communities engaged in civil society and political activity. Government Information Quarterly. 28, 2 (Apr. 2011), 148–154.
[4] Goffman, E. 1959. The Presentation of Self in Everyday Life.
[5] Kubicek, H. 2016. What Difference Does the “E” Make? Comparing Communication Channels in Public Consultation and Collaboration Processes. Evaluating e-Participation. G. Aichholzer et al., eds. Springer International Publishing. 307–331.
[6] Nonnecke, B. et al. 2004. What lurkers and posters think of each other [online community]. 37th Annual Hawaii International Conference on System Sciences, 2004. Proceedings of the. 0, C (2004), 1–9.
[6] Savolainen, R. 2008. Everyday information practice: a social phenomenological approach. Scarecrow Press.
[7] Svensson, J. 2017. Lurkers and the Fantasy of Persuasion in an Online Cultural Public Sphere. In press.
[8] Takahashi, M. et al. 2007. Active Lurking: Enhancing the Value of In-house Online Communities Through the Related Practices Around the Online Communities. Technical Report #4646–7.
[9] Wenger, E. 1998. Communities of Practice: Learning, Meaning and Identity. Cambridge University Press.